python逆向
3.8以上用pycdc
例题
Python逆向全版本MagicNumber表_python3.11.4 magicnumber-CSDN博客
例题(正常的py逆向)
enum PycMagic {
MAGIC_1_0 = 0x00999902,
MAGIC_1_1 = 0x00999903, /* Also covers 1.2 */
MAGIC_1_3 = 0x0A0D2E89,
MAGIC_1_4 = 0x0A0D1704,
MAGIC_1_5 = 0x0A0D4E99,
MAGIC_1_6 = 0x0A0DC4FC,
MAGIC_2_0 = 0x0A0DC687,
MAGIC_2_1 = 0x0A0DEB2A,
MAGIC_2_2 = 0x0A0DED2D,
MAGIC_2_3 = 0x0A0DF23B,
MAGIC_2_4 = 0x0A0DF26D,
MAGIC_2_5 = 0x0A0DF2B3,
MAGIC_2_6 = 0x0A0DF2D1,
MAGIC_2_7 = 0x0A0DF303,
MAGIC_3_0 = 0x0A0D0C3A,
MAGIC_3_1 = 0x0A0D0C4E,
MAGIC_3_2 = 0x0A0D0C6C,
MAGIC_3_3 = 0x0A0D0C9E,
MAGIC_3_4 = 0x0A0D0CEE,
MAGIC_3_5 = 0x0A0D0D16,
MAGIC_3_5_3 = 0x0A0D0D17,
MAGIC_3_6 = 0x0A0D0D33,
MAGIC_3_7 = 0x0A0D0D42,
MAGIC_3_8 = 0x0A0D0D55,
MAGIC_3_9 = 0x0A0D0D61,
MAGIC_3_10 = 0x0A0D0D6F,
MAGIC_3_11 = 0x0A0D0DA7,
MAGIC_3_12 = 0x0A0D0DCB,
INVALID = 0,
};
1、ezpy
exeinfope查壳,观察到pyinstaller字眼
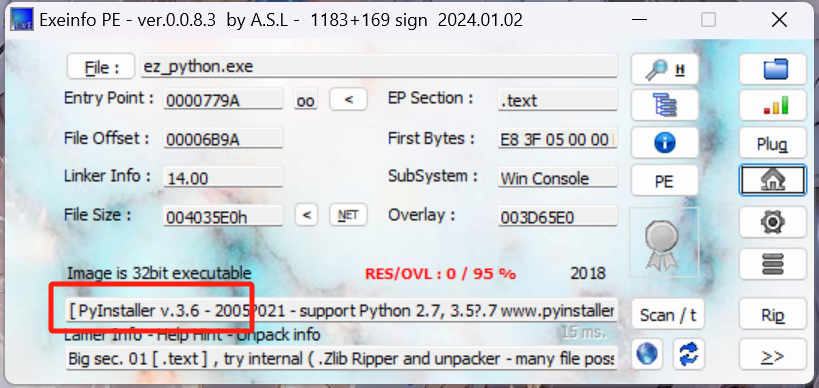
python逆向
pyinstxtractor下载链接->GitHub - extremecoders-re/pyinstxtractor: PyInstaller Extractor
uncompyle6库下载命令->cmd窗口输入【pip install uncompyle6】
这里已经下载完成了

然后进行反编译,在cmd窗口中输入命令【python pyinstxtractor.py 文件路径】
这里懒得输文件路径,索性直接拿到源代码文件下面

可以得到一个文件夹

此时在同目录下产生一个【xx.exe_extracted】文件夹,双击进入此文件夹,找到一个pyc文件(此处有两个文件,我们关注的是除struct.pyc外的另一个pyc文件,如下图红圈)

然后我们忽略那个struct.pyc ,对另外一个pyc进行反编译
在此处再次打开终端,输入命令【uncompyle6 src.pyc > src.py】之后即可在同目录下生成反编译的python文件


然后就可以看到反编译成功的py文件啦
 只要令flag=decrypt2(“AAAAAAAAAAAfFwwRSAIWWQ==”, key),key也已经说明
只要令flag=decrypt2(“AAAAAAAAAAAfFwwRSAIWWQ==”, key),key也已经说明
即可获得flag
1 | |
2、字符与长整型的转换
1 | |
1 | |
简单的来叙述一下这个exp。
首先因为他加密的时候是先套base58再套base64,所以我们解密的时候就要先解开base64再解base58。因为他在加密base58的时候有转换数据类型为str(字符串)。所以我们在解密base58的时候要转换数据类型为int(整数)。
第一步做完了。
第二步因为他在加密的时候使用了字节型转长整型。
所以我们解密的时候就要反过来把长整型转换成字节型。
1 | |
其实这一步做完之后我们已经把整个程序都解析完毕得到了flag为:HUBUCTF@1405
但是题目要求我们的最终flag还要进行一层md5加密。
所以我们得把HUBUCTF@1405进行md5加密一下,这里简单的方法可以使用在线网站直接加密。

或者就是用我exp里的办法python里的库函数进行python脚本里的md5加密。
最终的flag为:fd78ee3399dd6a3c1d0b637fdca0c075
最后这里附带上python脚本的运行结果:

3、nssctf2433
前面还是正常的python逆向
得到python文件
1 | |
exp
1 | |
Python逆向基本操作步骤详解——以杭电新生赛hgame week2 reverse stream(python3.10逆向)为例-CSDN博客magic number
3.8以下用compyle6
例题(修改文件头)
先对pyc反编译


使用010工具把struct的头八字节替换到1.pyc的最上面,为什么要替换?
因为用 PyInstaller 打包后,pyc 文件的前 8 个字节会被抹掉,所以最后要自己添加回去。前四个字节为 python 编译的版本,后四个字节为时间戳。想要获得编译版本可以查看打包文件里 struct 的信息,我这里还是提取出 struct 这个文件,有 struct 作为对照就方便多了,不用特定下载对应版本的 python 来生成特定的 pyc 文件来取前 8 个字节:

然后save,用在线的py反编译一下

1 | |
看到flag代码提取出来,注意这里要同时异或
1 | |
3、如果python版本不一样,那么反编译出来的py就不一样,所以得在线网站反编译

可以用在线网站查看python文件的版本

3.10.9的python反编译2.7的py就会出错的
1 | |
这是在线网站编译出来的正确文件
1 | |
附上re代码,
取余考查过很多次了记录一下,要保证在字符的范围内
1 | |
