暑假内部赛
MISC
小小侦探家

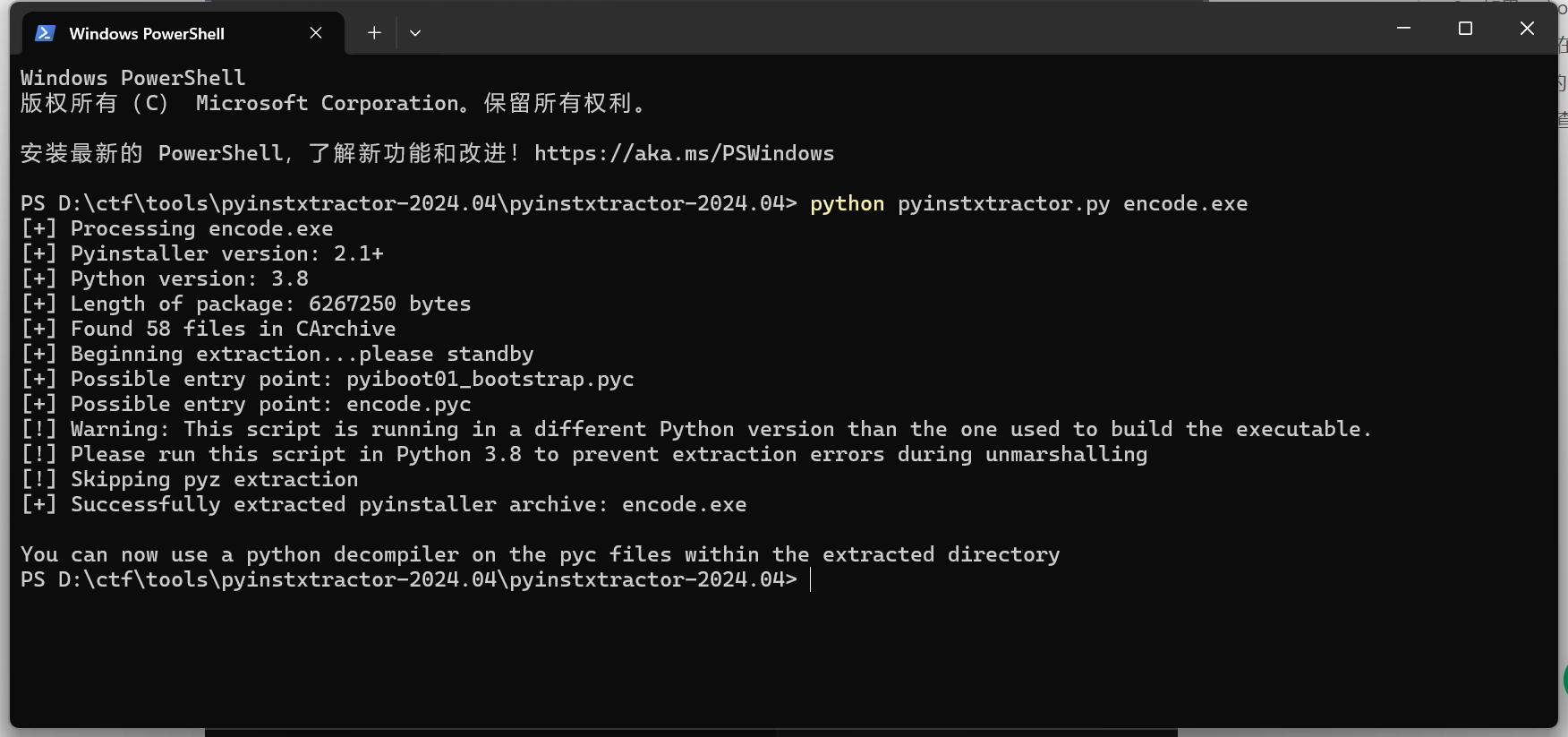

encode
1 | |
exp
1 | |

嗯,美国的朋友

正常


Matryoshka
exp
1 | |
然后爆破密码




改成zip然后解压缩

然后就拿到照片不会了

来自周神的万能py(伟大无需多言)

 \
\
sb0olI
WkpHU1VDVEZ7ODY1ODYzNkItNDJGMy0zNjQ4LTVCMjUtQUY2Q0RCRjI5NTI5fQ==

CRYPTO
phi
1 | |
basic_RSA
获得p,q
1 | |
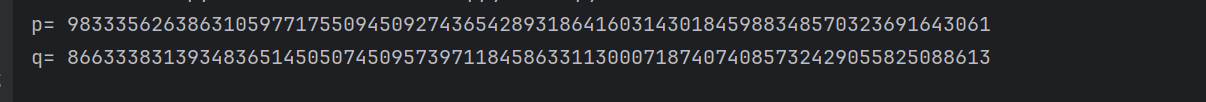
解密
1 | |

enc
1 | |
BASIC_rsa?
得到十进制的p

exp
1 | |

common(多组nc)
1 | |

RE
Hard_Signin
ida打不开,题目说文件被改了,放到010看一下

发现头被改了
正常的头

改回来就可以看到有个upx壳了


脱壳后放入ida得到flag

不要非预期

Python_Revenge
3.10
magic number 6F 0D 0D 61

将后缀改成pyc
放到kali里面用pycdc反编译

1 | |
exp
1 | |

Assembly_Yao
edx=‘@’ 0x40

暑假内部赛
http://example.com/2024/08/21/暑假内部赛/