MOECTF 2024
签到
跟着pdf
输入/bind 和个人识别码
MISC
signin
把luo缺勤,别的签到就行


罗小黑战记
gif图直接逐帧分析就行


moectf{y0uu6r3th3m0st3r1nth1sf13ld}
ez_F5
看属性里面

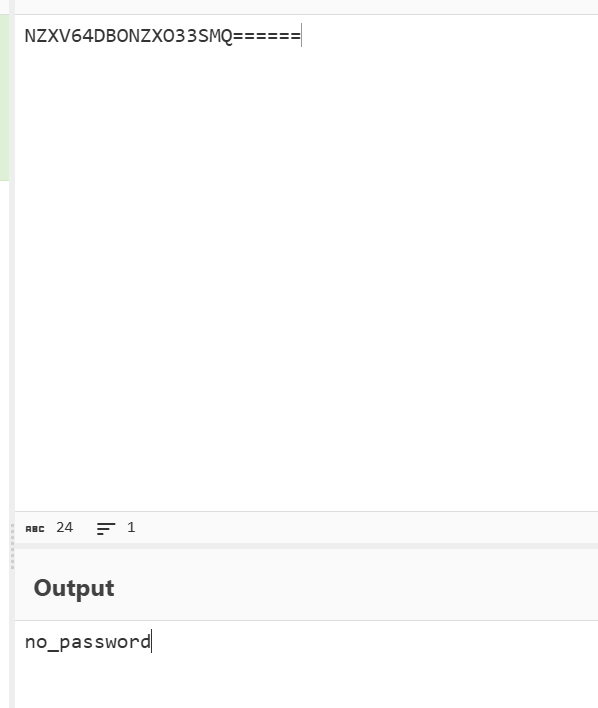
密码就是这个(当时真的无语住了)no_password


ez_Forensics
杂项入门指北

仔细观察,发现摩斯密码加密密文
注意中间要空格

the_secret_of_snowball
发现文件头错了
是ff d8


moectf{Welc0me_t0_the_secret_life_0f_Misc!}


提交发现错了。那应该不是
ret_life_0f_Misc!
find_it
查看西安的桔子水晶酒店,发现北站市政府店附近有相似的建筑


旋转视角
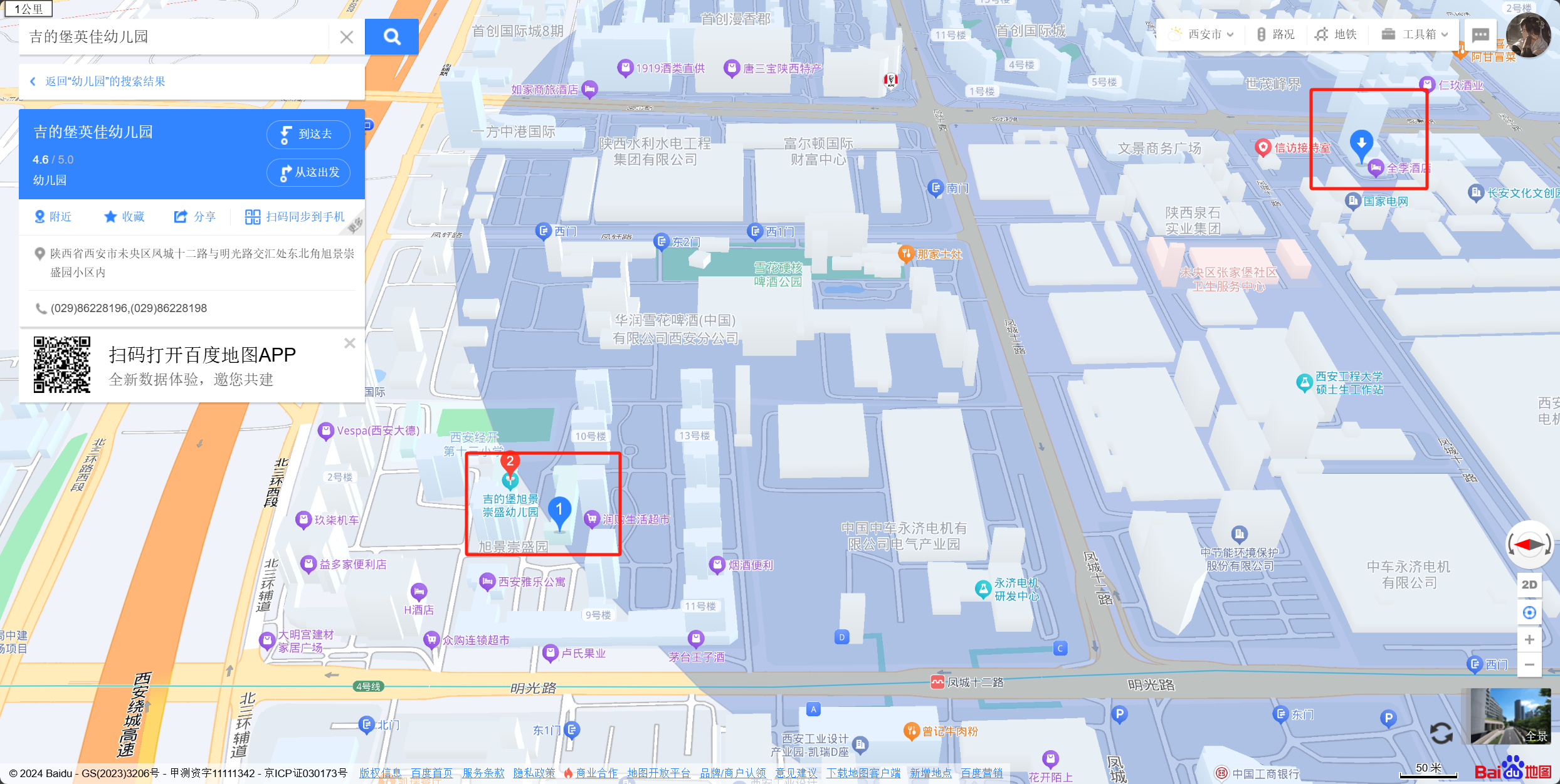
发现两个贴在一起的幼儿园

moectf{ji_di_bao_you_er_yuan}
解不完的压缩包
这里附上爆破脚本(使用时记得修改初始设置)
1 | |
拿到1.zip

发现解压要密码

crcexp
1 | |

密码*m:#P7j0

小小套娃
打开png发现文件出错

爆破宽高

拿到kali里面分离一下


改成png文件,扫码得到first key 874jfy37yf37y7

打开txt文件,发现显示长度与所见长度不合,是txt零宽度隐写

放入kali里面
用vi +文件名 命令打开
很明显是零宽度字符隐写,在上面有找到4种零宽度字符,使用在线解密工具进行解密
零宽文本加解密工具 - 翰络云工具 (hanloth.cn)
有feff、200f、200e、200b、200c

拿到密码,解一下佛教


拼图羔手
moejail_lv1

nc 127.0.0.1 63431

import(“os”).system(“ls”)

看一下main函数
1 | |
发现在另一个wrapper.sh里面

发现不能超过100个字符

ls /tmp -a 显示所有的文件,包括临时文件
使用通配符*省略后面的字符

moejail_lv2
Web
Web渗透测试与审计入门指北
安装phpstudy
Windows版phpstudy下载 - 小皮面板(phpstudy) (xp.cn)
本地搭建网站
一个视频教会你,如何在本地搭建php网站服务环境_哔哩哔哩_bilibili
创建一个目录,然后将www网站html放入目录中创建本地网站,访问local即可


弗拉格之地的入口

使用dirsearch扫描不出来
访问robots.txt
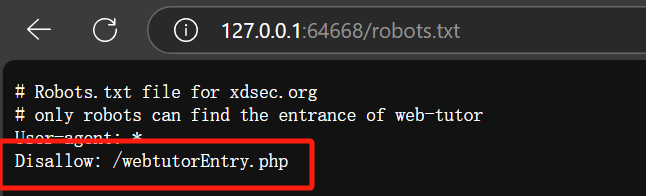
访问他给的地址拿到flag

ez_http

垫刀之路01: MoeCTF?启动!(env查看环境变量)


查看根目录即可



RE
入门签到
运行代码就行

moectf{r3v3rs3_1s_a_long_long_way_to_explore}
xor


1 | |

upx



upx-revenge


正常应该是UPX

改回来解壳

dynamic

下个断点,动调一下

点开看一下v7

发现里面存储着flag

shift12提取一下

moectf{18d4c944-947c-4808-9536-c7d34d6b3827}
TEA


单独的xyz在十六进制下都是一位,算半字节,<<16左移两字节
四字节x 四字节y+z

前面是4个密钥
cmp比较最终的密文
exp
1 | |

moectf{xxxxxxxx-yyyy-zzzz-9c42-caf30620caaf}
moectf{836153A5-8E00-49BD-9c42-caf30620caaf}
moectf{836153a5-8e00-49bd-9c42-caf30620caaf}(改成小写就对了)
xtea


moectf{your key}
d0tN3t
用ilspy打开

exp
1 | |
取余前:

取余后

rc4

exp
1 | |
babe-ze3(不会)

先脱壳

网站Hint最后一个if有问题,狗屁通说v4和 !(_DWORD)v4无法同时成立
之前Z3解密用的都是Ints类型,这次运算有变,变成BitVec()位向量
1 | |
moectf{9c0525dcbadf4cbd9715067159453e74}
xor(大嘘)

ez_maze

脱壳


Crypto
入门指北
1 | |
signin
1 | |

ez_hash
1 | |
exp
1 | |

moectf{2100360168}
Big and small(e很小)
1 | |
exp
1 | |
