0xGAME 2024
MISC
base2048

一明一暗
报告哈基米
长宽一样



zsteg看隐写

1 | |

0xGame{hajimi_i5_

看到末尾有个zip的反转数据,找一下末尾,然后导出逆向一下

1 | |
保存为zip文件



也有相关的在线网站可以解
tupperexp
1 | |
倒序一下数据再生成照片


倒过来看一下

Cute_r1ght?}
诗人握持

Web
Re
BabyBase

BinaryMaster
xor
看汇编把数据打印下来

1 | |
Xor-Endian
后往前读,最高位只有一位时补齐0

1 | |
upx


- 这里的逻辑对每个字节执行如下操作:
*v2 = (16 * *v2) | (*v2 >> 4);- 这个表达式将字节左移 4 位,然后将高 4 位通过右移操作保留并通过
|操作拼接到低 4 位。 - 换句话说,左移使低 4 位变为 0,高 4 位占据低 4 位,然后用原先的高 4 位来填充新生成的高 4 位。
- 这个表达式将字节左移 4 位,然后将高 4 位通过右移操作保留并通过
- 该操作对字符串的每个字节都重复,直到遇到
0(字符串结束符或空字节)。
为了逆向该过程,我们需要恢复原始的字节。给定编码后的字节值,我们可以通过以下操作恢复原始值:
- 将编码后的字节右移 4 位,以获取原始字节的高 4 位。
- 将编码后的字节进行掩码操作(与
0x0F)保留低 4 位,恢复原始字节的低 4 位。
1 | |
Ezjar

求逆元
5x =1mod 16
16 =5*3+1
5=5*1
1=16-5*3
-3 mod 16=13
1 | |
Ezpyc

1 | |
Xor::Ramdom
动态看v21的值 v21是0x7b


1 | |
ZZZ



注意开头38*这个数据不是0x,要转化成16进制

1 | |

注意最后的结果要倒序过来
ASM


1 | |
TEA

littlepuzzle
看到数组
提示密码是48位,所以最后输入的是解出来的数字





pypro(python-version3.12)
 看到他是3.8以上的pyc,所以用pycdc来反编译
看到他是3.8以上的pyc,所以用pycdc来反编译

这边不管使用uncompyle6还是pycdc都无法完全编译,使用pycdas查看字节码

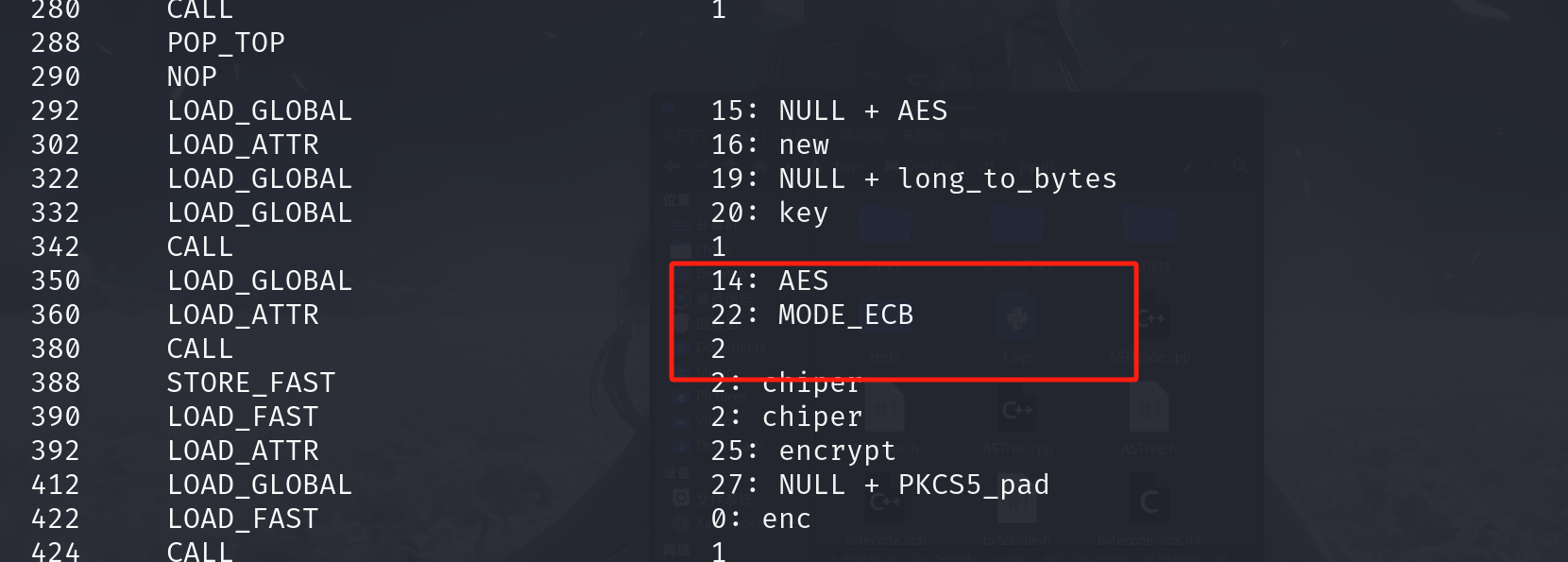
看到加密的有base64,AES,运算模式是ECB,填充类型是PKCS5
上饶ctf 逆向 pvm.exe_pycdc.exe 反编译不了全部代码-CSDN博客
1 | |
拿出所有字节码看看,看到数据了
1 | |
分析说明
- 密钥:
key是一个16字节的AES密钥,以十六进制表示,并在程序中使用。 - PKCS5填充:
PKCS5_pad函数确保数据的长度达到48字节,填充方式是将缺少的字节用填充值填充。 - 输入验证:
- 输入的
flag必须为44字节长度,不符合长度则直接报错退出。 - 验证
flag的第7个字符为'{',且最后一个字符为'}',否则退出并提示格式错误。
- 输入的
- AES加密:
- 使用AES ECB模式加密填充后的数据,最终生成密文。
- Base64编码和比较:
- 对密文进行Base64编码,将编码结果与预期的字符串
expected_data进行比较。 - 如果匹配,输出“flag正确”;否则输出“错误”。
- 对密文进行Base64编码,将编码结果与预期的字符串
字节码中的细节
- 反编译时的
JUMP_BACKWARD和其他字节码指令实现了长度和格式的验证逻辑,以及字符位置的条件检查。 - 出现的部分冗余指令可以忽略,因为它们不影响核心逻辑的理解和执行。
1 | |

MineSweeper
Crypto
caeser
直接爆破
code

0xGAME 2024
http://example.com/2024/12/08/0xGame 2024/